Working from home offers unparalleled flexibility, allowing employees to achieve a better work-life balance and avoid the daily commute. However, this shift also brings increased cybersecurity challenges.
With more people accessing company networks from home, the risk of cyber threats like ransomware attacks and data breaches has surged. Research confirms that since COVID-19, the FBI has reported a 300% increase in cyberattacks.
As Jason Harlam, Business Development Manager at Technology Advisory Group, says, “Robust cybersecurity practices are non-negotiable for safe and efficient remote work operations.”
As National Work From Home Day approaches, it’s crucial to prioritize cybersecurity to protect both personal and professional information. Here are the top cybersecurity tips to help you stay safe while working remotely.
Say Goodbye to Remote Work-Causing Security Nightmares!TAG fortifies your remote environment against cyber threats. |
Key Tips to Boost Your Cybersecurity on National Work From Home Day
1. Use Strong and Unique Passwords
One of the simplest yet most effective cybersecurity measures is enforcing the use of strong and unique passwords for all employee accounts. Remote employees should avoid easily guessable passwords like “password123” or “admin.”
Additionally, passwords should not be reused across multiple accounts. Consider implementing a company-wide password manager to help employees securely manage their credentials.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security to employee accounts by requiring a second form of verification and a password.
This could be a text message code, an email, or an authentication app. Enabling 2FA can significantly reduce the risk of unauthorized access to sensitive company information. Ensure that 2FA is enabled on all critical systems and accounts within your organization.
3. Update Software Regularly
Cybercriminals often exploit vulnerabilities in outdated software. Ensure that all employee devices, including operating systems, antivirus programs, web browsers, and any other software, are always up to date.
Most software allows automatic updates, which can help your company stay protected against the latest threats. Encourage your remote workforce to regularly check for and install updates.
4. Be Wary of Phishing Attacks
Phishing attacks involve cybercriminals sending fraudulent messages, often via email, that appear to be from legitimate sources. These messages aim to trick employees into revealing personal information or clicking on malicious links.
Train your remote staff to verify the sender’s email address, look for suspicious language, and avoid clicking on links or downloading attachments from unknown sources. Since 95% of cybersecurity breaches are due to human error, regular security awareness training is important to help employees recognize and respond to phishing attempts.
5. Secure Home Networks
A secure home network is crucial for remote work. Provide your remote workforce with guidelines on how to secure their home networks.
This includes changing the default username and password of their router, enabling WPA3 encryption if the router supports it, and ensuring that their Wi-Fi network is password protected. Additionally, suggest setting up a guest network for visitors to prevent them from accessing the primary network.
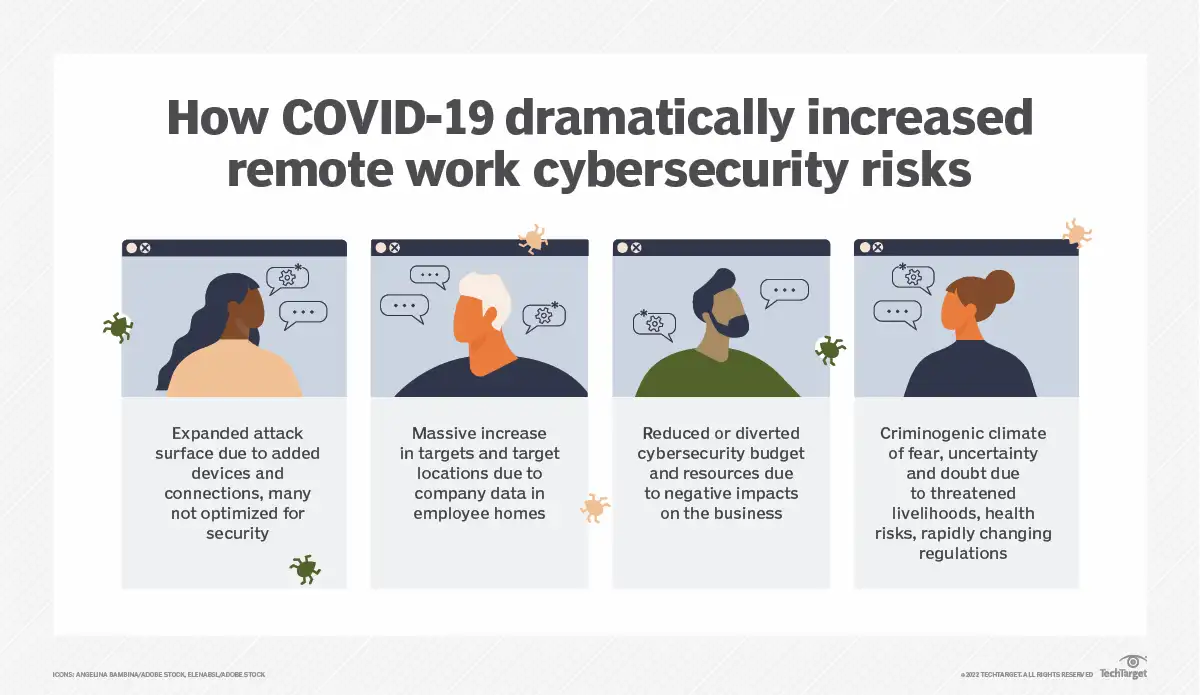
Source: TechTarget
6. Use a Virtual Private Network (VPN)
A VPN encrypts internet connections, making it harder for cybercriminals to intercept data. Using a VPN is especially important when employees access company resources remotely or use public Wi-Fi networks. Ensure your VPN service is reputable and offers robust encryption. Make it mandatory for employees to use a VPN when accessing company systems.
7. Backup Data Regularly
Regular data backups can save your company in the event of a cyber attack, such as ransomware. Implement a company-wide data backup policy that includes backing up data to an external hard drive or a cloud-based service.
Ensure that backups are performed regularly and that data can be easily restored if needed. Test the backup and restore process periodically to ensure its effectiveness.
8. Ensure Security in Co-Working Spaces
Co-working spaces offer flexible work options but also come with unique security risks. Employees using co-working spaces should use a VPN to secure their internet connection and avoid using public Wi-Fi for accessing sensitive information.
Encourage your remote employees to be mindful of their surroundings and avoid leaving their devices unattended. Additionally, ensure that any shared devices or networks in the co-working space are properly secured.
| More resources you might like: |
9. Implement Strong Endpoint Security
Ensure all work devices, including laptops, tablets, and smartphones, are protected with up-to-date antivirus software and firewalls.
Endpoint security solutions can help detect and prevent malware and other threats from compromising your devices. To maintain their effectiveness, regularly update and patch these security solutions.
10. Monitor for Unusual Activity
Regularly monitor your company’s accounts and devices for any unusual activity. This can include unexpected login attempts, unauthorized transactions, or sudden changes in system performance.
Early detection of suspicious activity can help prevent data breaches and other cyber incidents. Implement real-time monitoring tools to keep an eye on potential threats.
Cybersecurity Solutions to Strengthen Your Remote Work Security
| Service | Key Features | Benefits | Considerations |
| Endpoint Detection and Response (EDR) | Real-time monitoring, threat detection, automated response | Rapid identification and mitigation of threats | Requires integration with existing systems |
| Security Information and Event Management (SIEM) | Centralized logging, real-time analysis, incident response | Comprehensive visibility, improved compliance | Can be complex to set up and manage |
| Identity and Access Management (IAM) | User authentication, access control, single sign-on (SSO) | Enhanced security, streamlined user experience | May require user training |
| Cloud Security Solutions | Data encryption, threat detection, compliance management | Secure cloud environments, scalability | Dependent on the cloud provider’s security |
| Email Security Solutions | Phishing protection, spam filtering, malware detection | Reduced risk of email-based attacks | May require tuning to minimize false positives |
| Network Security Monitoring | Intrusion detection, traffic analysis, anomaly detection | Enhanced network visibility, proactive threat management | Needs continuous monitoring and maintenance |
| Data Loss Prevention (DLP) | Data encryption, monitoring, policy enforcement | Prevents unauthorized data sharing, ensures compliance | Can be resource-intensive to implement |
At Technology Advisory Group, we understand the complexities of cybersecurity in a remote working environment. Our expert team is here to provide the solutions you need to safeguard your data and operations.
Contact us today to schedule a free consultation and learn how we can help protect your business.
Schedule Your Cloud Services Consultation
Ready to make a move to the cloud? TAG is ready to help with any or all cloud services from a private cloud, public cloud, or Microsoft 365 services.


