As more businesses move to the cloud, cloud security assessments have become essential for safeguarding sensitive data. However, many companies fail to assess their cloud infrastructure regularly, leaving critical security gaps.
In fact, 80% of companies have encountered an increase in the frequency of cloud attacks.
Jason Harlam, Business Development Manager at Technology Advisory Group, emphasized, “Cloud security must be prioritized, and consistent assessments are key to identifying and remediating any vulnerabilities.”
Staying ahead of potential risks puts you in a better position to protect your business and meet compliance standards.
What is a Cloud Security Assessment?
A cloud security assessment is a process that evaluates the security of your cloud environment. It identifies vulnerabilities, compliance gaps, and other risks that could affect your business.
These assessments typically focus on security policies, data encryption, access control, and the overall health of your cloud systems.
Regular cloud assessments allow you to take proactive steps to prevent security threats and ensure that your business remains safe and compliant with industry regulations.
Strengthen Your Cloud Security TodayLet TAG safeguard your cloud environment with proactive and expert-driven cloud assessments. |
Key Components of a Cloud Security Assessment
A comprehensive cloud security risk assessment involves several critical steps. Understanding these elements can help you prioritize what matters most for your business.
1. Identifying Cloud Risks
A cloud risk assessment helps you identify potential risks, such as data breaches, misconfigurations, and non-compliance with industry standards. Without an assessment, you’re exposing your business to these risks.
2. Cloud Assessment Tools
To conduct a thorough assessment, you need the right tools. Cloud assessment tools can scan your infrastructure, identify weaknesses, and provide insights into areas that need improvement. These tools automate much of the process, saving time and reducing human error.
Why Your Business Needs Regular Cloud Risk Assessments
Cloud security risk assessments should not be a one-time thing. Instead, they should be conducted regularly to ensure your cloud environment remains secure.
A study found that human errors cause 55% of cloud data breaches. This highlights the need for continuous monitoring and assessments.
By conducting regular cloud risk assessments, you identify and address vulnerabilities before they become serious threats.
Cloud environments are dynamic. Changes in software, regulations, and threat landscapes make constant evaluation crucial.
Creating a Cloud Security Assessment Checklist
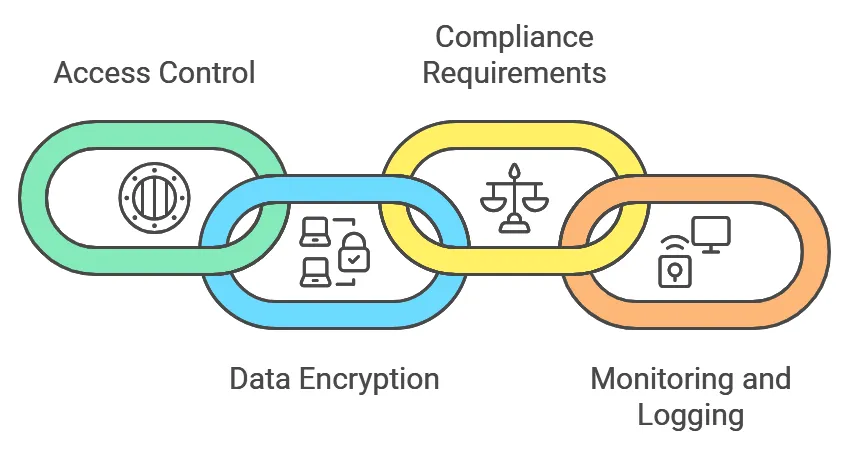
Having a cloud security assessment checklist ensures you don’t overlook any important details. Here are some key items to include:
- Access Control: Evaluate who can access sensitive data in your cloud environment. Use multi-factor authentication and least-privilege access to minimize risks.
- Data Encryption: Ensure all sensitive data is encrypted in transit and at rest. Encryption helps protect your data even if unauthorized access occurs.
- Compliance Requirements: Ensure your cloud infrastructure complies with industry standards like GDPR, HIPAA, and PCI-DSS. A cloud security risk assessment checklist will help you stay on track.
- Monitoring and Logging: Enable detailed monitoring and logging to track who accesses your data and what they do with it. This is essential for identifying suspicious activity and meeting regulatory requirements.
How to Conduct an Effective Cloud Security Assessment
To conduct a thorough cloud security assessment, follow these steps:
- Identify Key Assets
List all the data, applications, and services hosted in the cloud. Determine which are most critical to your business. - Assess Security Controls
Evaluate your current security policies, access controls, and encryption methods. - Conduct Vulnerability Scanning
Use cloud assessment tools to scan your infrastructure for weaknesses. These tools can pinpoint misconfigurations, outdated software, or other security gaps. - Review Compliance
Ensure your cloud environment complies with relevant industry standards. - Generate Reports and Take Action
Based on the findings, generate a report and develop an action plan to address any vulnerabilities.
Benefits of Proactive Cloud Security Assessments
According to CloudSecureTech, worldwide spending on data security has reached $81.6 billion. This shows that a proactive approach to cloud security assessments can save you money, time, and resources.
You reduce the likelihood of a data breach or service outage when you address potential risks early.
- Reduced Costs: Proactive assessments prevent costly damage control efforts after a security incident.
- Improved Compliance: Regular cloud risk assessments ensure your cloud environment meets industry regulations, avoiding penalties.
- Minimized Downtime: By identifying risks early, you can address them before they lead to system downtime or data loss.
| More resources you might like: |
Common Cloud Security Gaps and How Assessments Address Them
When it comes to cloud security, certain vulnerabilities often go unnoticed until it’s too late. A thorough cloud security assessment helps identify and address these gaps before they become major risks.
| Security Gap | How Cloud Security Assessments Address It |
| Lack of Multi-Factor Authentication (MFA) | Cloud assessments identify whether MFA is implemented across critical systems to ensure access control. |
| Unsecured APIs | Assessments evaluate API security to protect them against misuse and breaches. |
| Inadequate Data Encryption | Cloud security assessments check if sensitive data is encrypted in transit and at rest, reducing exposure. |
| Improper Cloud Configuration | Assessments audit configurations to identify misconfigured settings that could lead to vulnerabilities. |
| Unpatched Software and Vulnerabilities | Regular assessments detect unpatched systems, ensuring timely updates to minimize exploitation risks. |
| Overly Permissive Access Controls | Cloud assessments evaluate access controls and user permissions, recommending least-privilege practices to limit exposure. |
Strengthen Your Cloud Security with Expert Guidance
Cloud security is essential to your business’s success. Cloud security assessments help you identify and mitigate risks, ensure compliance, and protect sensitive data.
| Discover Trusted Cybersecurity Services Near You
|
At Technology Advisory Group, we provide cloud security assessments that give you peace of mind. Our proactive approach helps you stay ahead of potential threats and maintain a secure cloud environment.
With over 25 years in business and a track record of over 75 active clients, we have helped businesses reduce recurring IT issues and improve their security posture. Contact us today to schedule your consultation and take the first step toward a safer, more secure cloud infrastructure.
Schedule Your Cloud Services Consultation
Ready to make a move to the cloud? TAG is ready to help with any or all cloud services from a private cloud, public cloud, or Microsoft 365 services.


